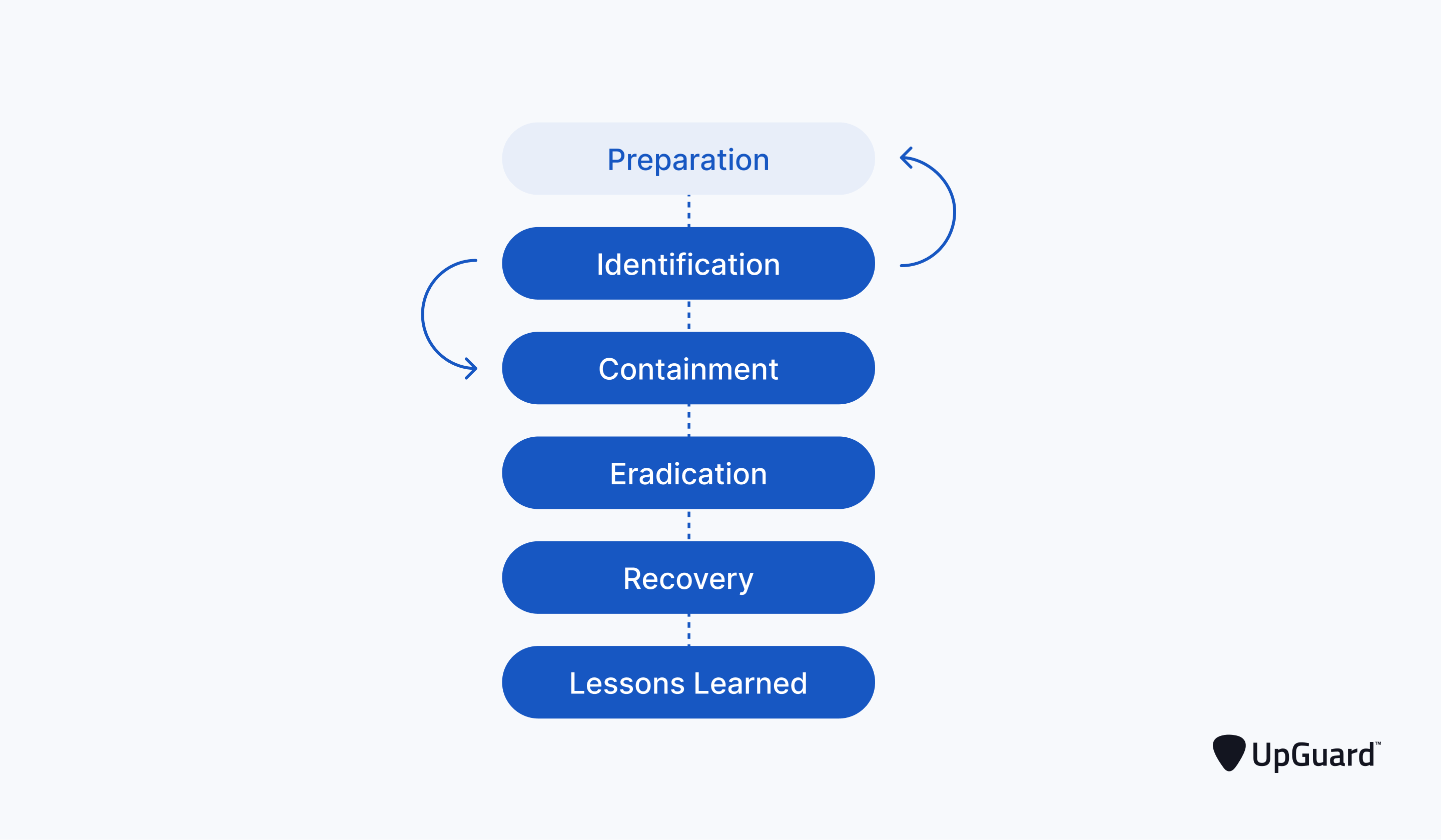
In the era of cloud computing, incident response planning is not a luxury but a necessity. This blog post will guide you through the crucial steps to develop a cloud-native incident response plan that will help your organization stay resilient in the face of evolving cyber threats. Read on to learn how to protect your cloud infrastructure and data effectively.
Tag: Incident Response
Cloud-Native Incident Response: Managing Security Breaches
As the digital world continues to evolve, so do the tactics of cybercriminals. To effectively combat security breaches, organizations must embrace cloud-native incident response strategies that align with the modern threat landscape. In this post, we delve into the key aspects of cloud-native incident response and offer actionable insights to strengthen your security posture.
Incident Response Planning: Developing a Comprehensive Strategy
In the age of cyber threats, having a well-defined incident response plan is not just a good practice; it’s a necessity. Read on to learn how to develop a comprehensive strategy to protect your organization from potential security incidents.
Advanced Persistent Threats (APTs): Detecting Long-Term Intrusions
In the ever-evolving landscape of cybersecurity, Advanced Persistent Threats (APTs) pose a significant challenge. This blog post delves into the world of APTs, their characteristics, and advanced techniques to detect and mitigate these long-term intrusions effectively.
Data Breaches: Impact, Prevention, and Response
In our increasingly digital world, data breaches have become a common concern. This blog post explores the impact of data breaches, effective prevention strategies, and how organizations can respond when their data security is compromised.
Cybersecurity Incident Response: Preparing for and Managing Breaches
Cybersecurity incidents are an unfortunate reality of the modern business landscape. In this blog post, we’ll delve into the world of cybersecurity incident response, helping you understand why preparation is crucial and how to manage breaches effectively.