In today’s digital age, the threat of cyberattacks looms large over organizations of all sizes and industries. With the ever-increasing sophistication of cybercriminals, it’s not a matter of if but when your organization will face a cybersecurity incident. The key to minimizing the damage and recovering swiftly lies in effective cybersecurity incident response. In this blog post, we’ll explore the importance of preparing for and managing breaches, and provide actionable steps to bolster your organization’s cyber resilience.
Understanding Cybersecurity Incidents
Before delving into the intricacies of incident response, it’s essential to understand what constitutes a cybersecurity incident. A cybersecurity incident is any event that jeopardizes the confidentiality, integrity, or availability of your organization’s digital assets. These incidents can take various forms, including:
Data Breaches: Unauthorized access to sensitive data, resulting in its exposure or theft.
Malware Attacks: Infiltration of malicious software into your systems, designed to disrupt operations or steal data.
Phishing Attacks: Deceptive emails or messages that trick employees into revealing sensitive information or granting access to cybercriminals.
Denial of Service (DoS) Attacks: Overwhelming your network or systems to render them inaccessible to legitimate users.
Each of these incidents poses a unique set of challenges, but the overarching principles of incident response remain consistent.
The Importance of Preparation
The old adage “an ounce of prevention is worth a pound of cure” holds true in the realm of cybersecurity. Preparation is the cornerstone of an effective incident response strategy. Here’s why it matters:
Minimizing Damage: A well-prepared organization can detect and respond to incidents more swiftly, limiting the potential harm caused by cyberattacks.
Reducing Downtime: Rapid response can help minimize downtime, ensuring that your business operations continue with minimal disruption.
Protecting Reputation: A well-handled incident can mitigate damage to your organization’s reputation, which is often one of the most significant casualties of a cyberattack.
Meeting Legal Requirements: Many jurisdictions require organizations to have incident response plans in place to comply with data protection laws and regulations.
Building a Cyber Resilience Framework
To prepare for cybersecurity incidents effectively, organizations should develop a cyber resilience framework that encompasses several key elements:
Risk Assessment: Begin by identifying and assessing potential risks and vulnerabilities in your organization’s digital infrastructure. This includes evaluating the value and sensitivity of your data, as well as the potential threats it faces.
Incident Response Plan: Develop a comprehensive incident response plan that outlines roles, responsibilities, and procedures to follow in the event of a cybersecurity incident. Ensure that all employees are aware of and trained in these protocols.
Security Tools and Technologies: Invest in state-of-the-art security tools and technologies, such as intrusion detection systems, firewalls, and antivirus software. Regularly update and patch these tools to stay ahead of evolving threats.
Monitoring and Detection: Implement robust monitoring systems that continuously scan your network for anomalies and potential breaches. Early detection can make all the difference in minimizing damage.
Data Backups: Regularly back up your critical data to secure, isolated locations. This ensures that even if your primary systems are compromised, you can recover your data.
Cyber Insurance: Consider obtaining cyber insurance to help cover the financial costs associated with a cybersecurity incident, including legal fees, data recovery, and customer notification.
Effective Incident Management
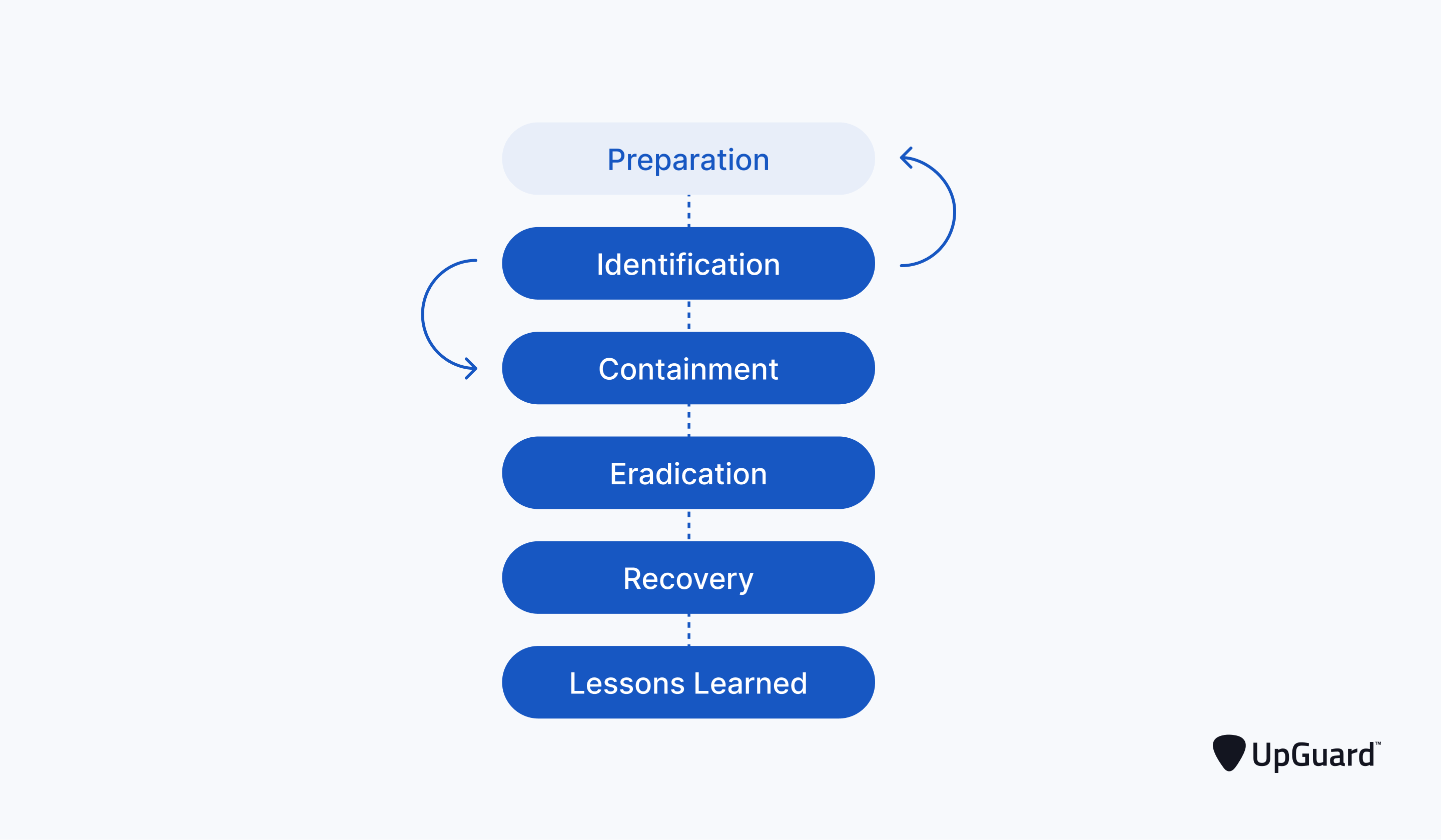
In the unfortunate event of a cybersecurity incident, a well-executed incident management plan is critical. Here are the steps to follow when managing a breach:
Identification: Quickly identify and confirm the nature of the incident. Is it a data breach, malware attack, or another type of cyber incident? The faster you know, the faster you can respond appropriately.
Containment: Isolate affected systems or networks to prevent the incident from spreading further. This might involve taking systems offline or disconnecting from the internet.
Eradication: Eliminate the root cause of the incident. This might involve removing malware, closing vulnerabilities, or patching systems.
Recovery: Begin the process of restoring affected systems to normal operation. This includes verifying the integrity of data and systems before bringing them back online.
Communication: Notify relevant stakeholders, including customers, employees, and regulatory authorities, as required by law. Transparency is crucial to maintaining trust.
Post-Incident Analysis: Conduct a thorough post-incident analysis to understand what went wrong and how to prevent similar incidents in the future. Adjust your incident response plan and security measures accordingly.
Continuous Improvement
Cybersecurity incident response is not a one-and-done task; it’s an ongoing process that requires continuous improvement. Regularly update and test your incident response plan, adapt to emerging threats, and ensure that your organization remains resilient in the face of evolving cybersecurity challenges.
Conclusion
In the digital age, cybersecurity incidents are a matter of when, not if. By prioritizing preparation and adopting a proactive stance, organizations can effectively manage breaches, minimize damage, and protect their valuable assets and reputation. Remember that cybersecurity is an ever-evolving field, so staying informed and continuously improving your incident response capabilities is essential to safeguarding your organization in an increasingly interconnected world.